Course Title: Information Security Risk Manager
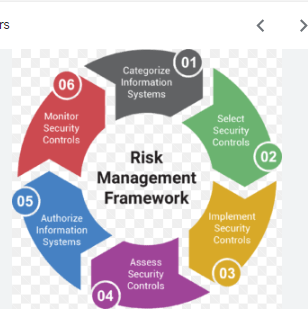
Course Title: Information Security Risk Manager Creating a comprehensive "Information Security Risk Manager" course involves covering various topics related to information security, risk assessment, and management. Below is an outline of the course, including key modules and their respective subtopics. This course is designed to help individuals understand and manage information security risks effectively. Course Description: This course equips individuals with the knowledge and skills needed to identify, assess, and manage information security risks within an organization. Participants will learn to implement risk management strategies and safeguard critical data assets. Course Outline: Module 1: Introduction to Information Security Risk Management Understanding Information Security Risk The Importance of Risk Management Risk Management Frameworks and Standards Module 2: Risk Identification Asset Inventory Threat Identification Vulnerability Assessment Module 3: Risk Ass...

