Course Title: Information Security Risk Manager
Course Title: Information Security Risk Manager
Creating a comprehensive "Information Security Risk Manager" course involves covering various topics related to information security, risk assessment, and management. Below is an outline of the course, including key modules and their respective subtopics. This course is designed to help individuals understand and manage information security risks effectively.
Course Description: This course equips individuals with the knowledge and skills needed to identify, assess, and manage information security risks within an organization. Participants will learn to implement risk management strategies and safeguard critical data assets.
Course Outline:
Module 1: Introduction to Information Security Risk Management
- Understanding Information Security Risk
- The Importance of Risk Management
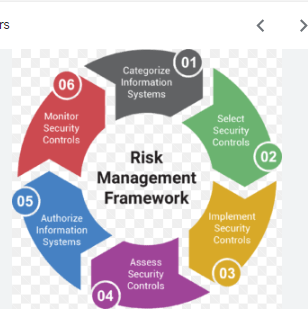
- Risk Management Frameworks and Standards
Module 2: Risk Identification
- Asset Inventory
- Threat Identification
- Vulnerability Assessment
Module 3: Risk Assessment
- Risk Analysis
- Qualitative vs. Quantitative Risk Assessment
- Calculating Risk Likelihood and Impact
Module 4: Risk Mitigation Strategies
- Risk Mitigation Planning
- Risk Mitigation Controls
- Cost-Benefit Analysis
Module 5: Risk Communication and Reporting
- Effective Risk Communication
- Risk Reporting to Stakeholders
- Risk Registers and Documentation
Module 6: Compliance and Regulatory Requirements
- Legal and Regulatory Frameworks
- Data Protection Laws
- Industry-Specific Compliance
Module 7: Business Continuity and Disaster Recovery Planning
- Risk and Business Continuity Planning
- Disaster Recovery Planning
- Incident Response Procedures
Module 8: Security Policies and Procedures
- Developing Security Policies
- Procedure Development and Implementation
- Policy Enforcement
Module 9: Security Technologies and Tools
- Risk Assessment Tools
- Security Information and Event Management (SIEM)
- Intrusion Detection and Prevention Systems (IDPS)
Module 10: Security Auditing and Assessment
- Conducting Security Audits
- Third-Party Risk Assessments
- Continuous Monitoring
Module 11: Case Studies and Practical Scenarios
- Real-World Information Security Risk Scenarios
- Analyzing Historical Security Incidents
Module 12: Ethical and Legal Aspects of Risk Management
- Ethical Considerations in Risk Management
- Legal Obligations and Liabilities
Module 13: Emerging Trends in Information Security Risk Management
- Cybersecurity Threats and Trends
- Future Challenges and Opportunities
Module 14: Final Project and Certification
- Practical Risk Assessment Project
- Course Review and Certification Examination
Course Delivery Method:
- The course can be delivered through a combination of in-person and online instruction.
- Practical exercises, group discussions, and case studies are used to reinforce learning.
Target Audience:
- Information security professionals, risk managers, IT managers, compliance officers, and anyone responsible for securing an organization's information assets.
Prerequisites:
- Participants should have a basic understanding of information security concepts and some experience in IT or cybersecurity.
Assessment:
- Regular quizzes, assignments, and a final project assessment.
- Certification is awarded upon successful completion.

Comments
Post a Comment